
The Black Basta ransomware group has emerged as one of the most impactful cyber threats in recent years. Known for their sophisticated operations and the use of a Ransomware-as-a-Service (RaaS) model, insight into their tactics has significantly expanded following a major leak of internal chat logs. Released by a Telegram user in 2024, these logs unveil the group’s methods, targets, and potential threats, drawing parallels with the notorious Conti leaks of 2022. This article delves into the operations of Black Basta, their recent activities, and the broader implications for global cybersecurity.
The recent leaks involving Black Basta provide an intricate look into the inner workings of a ransomware group that has had a significant impact since its emergence in 2022. These leaks became available to the public through a file disseminated on the messaging platform Telegram by a user known as ExploitWhispers. Utilizing Telegram as the medium for this release highlighted the platform’s potential as an effective conduit for distributing sensitive information quickly and widely, though with its own set of privacy and operational risks.
Introduction to Black Basta and Recent Leaks
The chat logs, numbering around 200,000 messages, peeled back the layers on Black Basta’s operational strategies, targets, and internal communications. Analysis of these logs revealed tactics and techniques employed by the group, such as credential access through the Mimikatz tool and command and control through the AnyDesk application. Notably, the group used typical reconnaissance tools and strategies to evade defenses, such as employing temp directories and tampering with Windows Defender, suggesting a sophisticated understanding of their targets’ environments.
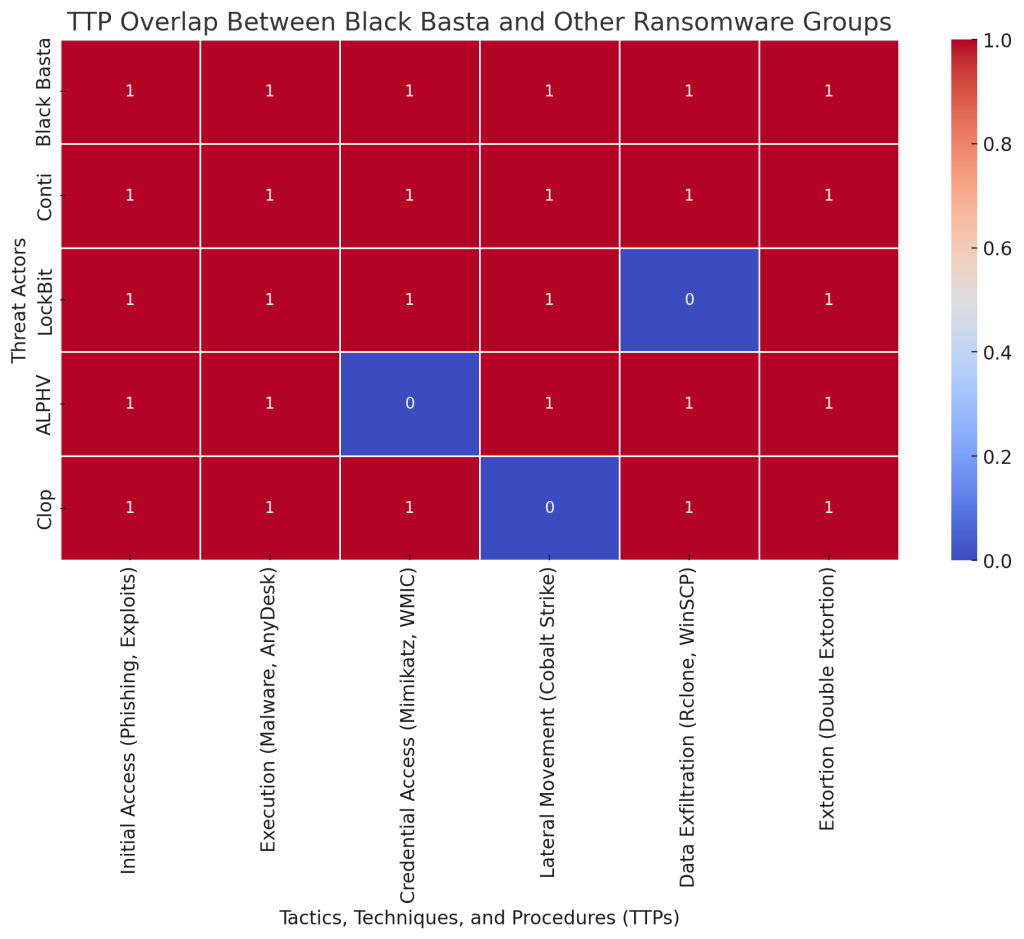
Comparing these leaks to the Conti leaks from 2022 shows both continuity and evolution in ransomware operations. Both events exposed the methodological depths of ransomware groups, yet Black Basta’s leaks reflect a more refined approach to extortion, incorporating lessons from predecessors. While both leaks underscore the importance of cybersecurity readiness, the Black Basta leaks uniquely underline how ransomware groups are learning from each other’s exposes and tightening their own operational security in response. Despite facing breaches, these groups continue to evolve within the cybercriminal ecosystem, posing persistent threats.
Detailed Analysis of the Leak
An in-depth analysis of Black Basta’s leaked operations reveals much about the platform choices and their influence on public exposure. The data was dispersed on Telegram by an entity called ExploitWhispers, demonstrating how secure messaging apps may facilitate wide dissemination of sensitive materials. While effective in reaching a broad audience, using such public, traceable methods raises questions regarding the motivations for choosing this platform for a leak and not more clandestine channels.
The leaked chat logs, totaling 200,000 messages, provide an unprecedented window into Black Basta’s tactics, revealing extensive use of familiar reconnaissance tools like ifconfig.exe and netstat.exe, alongside defense evasion tactics such as BITS component abuse. Insights into their credential access strategies show the reliance on Mimikatz, while command and control relied on AnyDesk. The logs confirm a scattergun approach to data exfiltration using Rclone utilities, emphasizing persistence through scheduled tasks.
Comparing these revelations to the Conti leaks of 2022 highlights both evolution and consistency in ransomware methodologies. Both leaks exposed foundational tactics and techniques in ransomware operations that have persisted across time. However, Black Basta’s advancements suggest an adaptation of methodologies following public exposure from previous leaks, utilizing better evasion techniques and novel exfiltration methods. Hence, these leaks not only expose technical vulnerabilities but also highlight a progressive learning curve among cybercriminals under scrutiny.
Threat Profile and Global Impact
The leak of Black Basta’s internal chat logs provided significant insights into their operations and threat profile, revealing novel Tactics, Techniques, and Procedures (TTPs) that enhance their operational effectiveness. Newly identified methods included reconnaissance tools like ifconfig.exe, netstat.exe, and WMIC abuse, defense evasion through temp directories and BITS component misuse, and credential access via Mimikatz. Additionally, command and control were facilitated through AnyDesk, and data exfiltration executed with Rclone.
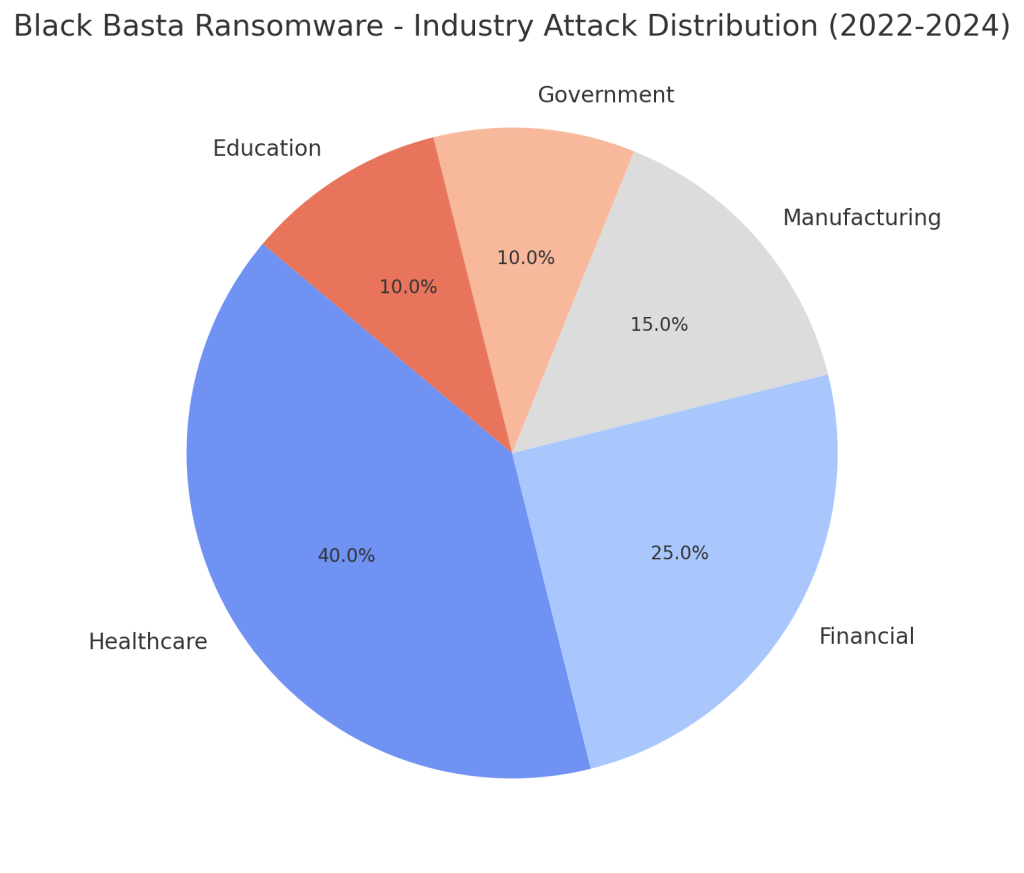
The impact of Black Basta’s ransomware primarily targets critical infrastructures and high-stakes sectors, notably healthcare, exacerbating global cybersecurity concerns. According to reports from the Cybersecurity & Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI), Black Basta launched attacks on over 500 entities spanning North America, Europe, and Australia, affecting 12 out of 16 critical infrastructure sectors. The ripple effect of these assaults is particularly pronounced in healthcare due to potential patient safety concerns and the sector’s intrinsic vulnerabilities.
The stark rise in threat levels underscores a desperate need for enhanced security measures. The global footprint of Black Basta’s actions compels a reassessment of threat management protocols, with intensified focus on sectors most prone to ransomware-related disruptions. The accumulated data from these leaks not only unravels operational themes but also propels the ongoing evolution of cybersecurity frameworks to counteract such menaces.
Operational Exam: Tactics and Business Model
Black Basta’s operational methodologies are intricately structured around the Ransomware-as-a-Service (RaaS) model, which facilitates widespread attacks through a network of affiliates. Their initial access techniques primarily involve phishing emails containing malicious links or attachments, alongside exploiting known software vulnerabilities. Upon initial access, they employ sophisticated defense evasion tactics, including the use of Anydesk for remote control and the Backstab tool to disable antivirus protections.
Exfiltration methods identified from leaked logs reveal a reliance on Rclone and WinSCP, suggesting a preference for utilizing known and trusted utilities to transfer data. These tactics are complemented by lateral movement within networks using tools like SoftPerfect and Cobalt Strike beacons, enabling comprehensive reconnaissance and data collection before execution of ransomware.
Black Basta’s signature strategy involves ‘double extortion,’ where victims are forced to pay not only to decrypt their data but also to prevent the public release of sensitive information exfiltrated prior to encryption. Understanding and mitigating such tactics is crucial for defense systems, emphasizing the need for robust multi-layered security measures to detect and block initial infiltration attempts, track unusual data transfers, and secure critical assets.
As ransomware groups like Black Basta continue to evolve, they underscore the increasing threat from RaaS models, where operational complexities extend well beyond mere encryption into sophisticated negotiation and extortion tactics. This multifaceted approach necessitates a comprehensive security posture, prioritizing both prevention and rapid incident response to minimize ransomware impact.
Recent Activity Reports
Navigating through recent reports on Black Basta’s activity illuminates the significant strides they have made in adapting their strategies over time. A notable comprehensive report published by the Cybersecurity & Infrastructure Security Agency (CISA) and the FBI outlines Black Basta’s operational game plan, drawing attention to their systemic and tactical maneuvers which have enhanced their grip on public and private sector entities globally.
This report highlights a series of tactical approaches, foremost among them being the exploitation of known software vulnerabilities and the aggressive deployment of phishing campaigns to gain initial access to systems. The integration of tools like AnyDesk for remote control and backdoor functionality showcases their sophisticated defense evasion capabilities, significantly challenging traditional defensive measures.
The healthcare sector emerges as a primary focus of Black Basta’s operations, along with financial infrastructure, reflecting their penchant for high-impact targets. Other targeted regions include North America, Europe, and the Asia-Pacific territories, marking a broad geographical footprint. The report cites over 500 instances of targeted entities from various critical infrastructure sectors between 2022 and 2024, underscoring a formidable threat landscape.
This rising threat level emphasizes the critical need for bolstered cybersecurity protocols, with a focus on early detection and rapid incident response capabilities to mitigate potential disruptions. The legacy of Black Basta’s attacks has left a telling impact on the current cybersecurity strategies, necessitating a multi-layered approach to both prevention and mitigation in the face of evolving cyber-adversaries.
Advanced Threat Analysis and External Resources
This advanced threat analysis of Black Basta reveals a sophisticated operation leveraging the Ransomware-as-a-Service (RaaS) model, enhancing their efficiency and reach through an extensive network of affiliates. These affiliates often spearhead phishing campaigns, a primary access vector, where emails are loaded with malicious attachments or links. These campaigns eventually segue into direct contacts, often under the guise of IT support to deploy remote access tools masquerading as legitimate software updates, an approach that has seen considerable success.
The exploitation of software vulnerabilities remains a staple in Black Basta’s strategy, with case studies highlighting aggressive manipulation of known vulnerabilities such as CVE-2021-1675 and CVE-2021-34527. These hacks open pathways for further operations involving tools like Mimikatz for credential harvesting and AnyDesk for command and control purposes, indicative of their capability for lateral movement and in-depth penetration of targets.
Recent incidents and their repercussions emphasize the need for robust threat intelligence alliances. Organizations are encouraged to utilize MITRE ATT&CK references, which catalog tactics like exfiltration over alternative protocols and command-line interface manipulation, providing a framework for understanding and mitigating such threats.
Security practitioners should incorporate related threat packages and hunting guides, like those identified by Intel 471, to track tell-tale indicators of compromise (IOCs) efficiently. Understanding these methodologies not only helps in preparing organizations for known threats but also builds resilience against evolving tactics.
Moreover, resources like CISA advisories and multi-national incident reports underscore the international scale of the threat Black Basta represents. As their tactics evolve, maintaining an informed stance through these resources becomes imperative for continued resilience against ransomware activities.
These insights not only reinforce the importance of preventative measures, like multi-factor authentication and regular patch updates but also highlight the critical role of education and awareness within organizations, enabling them to effectively recognize and respond to phishing and social engineering attacks.
Conclusions
This in-depth analysis of Black Basta’s operations and the recent leak offers significant insights into one of the most advanced ransomware groups today. By scrutinizing their Tactics, Techniques, and Procedures, and comparing their activities over time, we grasp the evolving nature of ransomware threats. The implications for global cybersecurity are profound, urging both public and private sectors to implement robust defense mechanisms and collaborate internationally to mitigate such threats effectively in the future.

GreyFriar
NateW (GreyFriar) is a seasoned Cyber Threat Intelligence Analyst with a deep focus on AI, cybersecurity, and threat research. With over two decades in the field, he delivers insights on evolving cyber threats, adversary tactics, and AI-driven security innovations.
💡 If you enjoyed this post, leave a comment—I’d be happy to respond! A like on this post helps my site grow and reach more people interested in cybersecurity and AI intelligence.
For more insights, follow me on X (Twitter), LinkedIn, and Medium or visit my blog, Cyber Intel AI.

Great content! Super high-quality! Keep it up! http://www.hairstylesvip.com
Good web site! I truly love how it is easy on my eyes and the data are well written. http://www.hairstylesvip.com I am wondering how I could be notified whenever a new post has been made. I’ve subscribed to your RSS which must do the trick! Have a nice day!