Understanding and Implementing Cyber Threat Intelligence for SMBs: A Comprehensive Guide
In today’s digital landscape, cyber threat intelligence (CTI) has evolved from a nice-to-have security measure to an essential component for businesses of all sizes. Small and medium-sized businesses (SMBs) are increasingly finding themselves in the crosshairs of sophisticated cybercriminals, making robust cyber threat intelligence more crucial than ever. This guide will walk you through what CTI is, why it matters for your business, and practical steps to implement it effectively—even with limited resources.
Estimated Reading Time
15 minutes
Key Takeaways
- Cyber threat intelligence (CTI) is essential for SMBs.
- CTI offers actionable insights into cyber threats.
- SMBs can leverage CTI to improve security posture and meet compliance.
- Effective CTI implementation requires clear objectives, asset identification, and appropriate tools.
- Automation can enhance SMBs’ CTI programs.
Table of Contents
- What is Cyber Threat Intelligence?
- The Critical Importance of CTI for Small and Medium Businesses
- The Four Key Components of Threat Intelligence
- Understanding Cyber Risk Intelligence
- Practical CTI Implementation for SMBs
- Leveraging Automation in Your CTI Program
What is Cyber Threat Intelligence?
Cyber threat intelligence is the systematic collection, analysis, and distribution of information about potential or active cyber threats targeting your organization’s digital assets. Unlike traditional cybersecurity approaches that focus primarily on defense, CTI takes a proactive stance by providing actionable insights into the who, what, why, and how of cyber threats.
At its core, CTI helps you understand:
- The tactics, techniques, and procedures (TTPs) used by threat actors
- The specific threats most likely to target your industry or business model
- How to prioritize your security efforts based on actual risk
- Ways to strengthen your security posture against emerging threats
Cyber threat intelligence converts data into meaningful information to identify, assess, and respond to cyber threats with informed decision-making, notes cybersecurity experts at CyberMaxx.
The Critical Importance of CTI for Small and Medium Businesses
You might think cyber threat intelligence is only for large enterprises with massive security budgets. The reality couldn’t be more different. SMBs are increasingly attractive targets for cybercriminals for several compelling reasons:
- Limited security resources: Most SMBs lack dedicated security teams or substantial security budgets
- Valuable data assets: Even small businesses process customer information, financial records, and intellectual property
- Supply chain vulnerability: SMBs often serve as entry points to larger organizations
- Less sophisticated defenses: Many SMBs rely on basic security tools that sophisticated attackers can easily bypass
According to recent studies, 43% of cyber attacks specifically target small businesses, yet only 14% are prepared to defend themselves. Implementing even basic CTI can dramatically improve your security posture without breaking the bank.
For SMBs, cyber threat intelligence provides several critical benefits:
- Risk prioritization: Focus limited resources on the most likely and damaging threats
- Improved incident response: Respond faster and more effectively when incidents occur
- Better security investments: Make informed decisions about security tools and services
- Regulatory compliance: Meet growing compliance requirements for data protection
- Business continuity: Minimize disruptions from successful attacks
By leveraging CTI appropriately, even small businesses can develop enterprise-grade threat awareness and response capabilities.
Read more here.
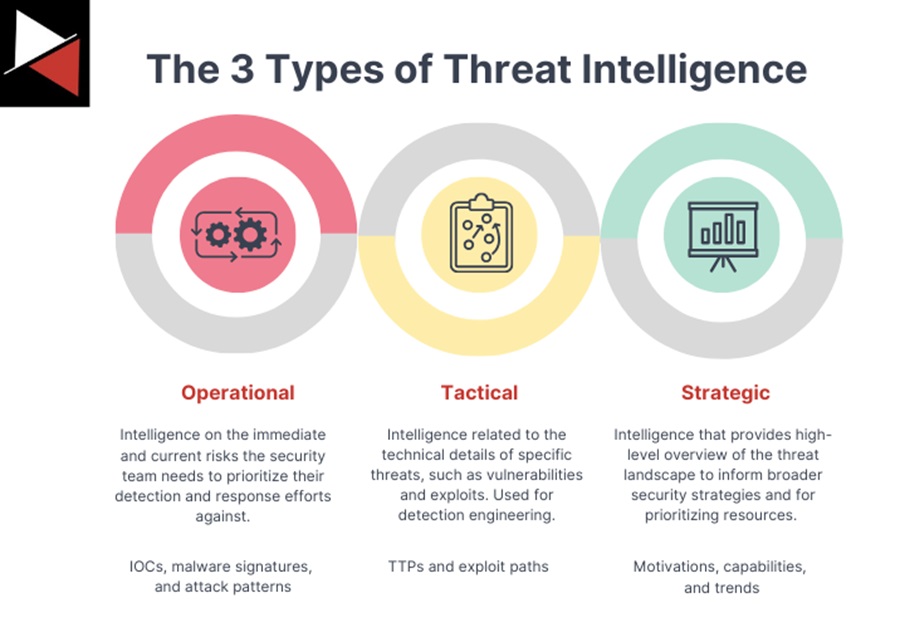
The Four Key Components of Threat Intelligence
Effective cyber threat intelligence operates at multiple levels, each serving different stakeholders and purposes within your organization. Understanding these components helps you implement a balanced CTI program:
1. Strategic Intelligence
Strategic intelligence provides high-level insights designed for executive decision-makers and board members. This type of intelligence focuses on:
- Broad threat landscapes affecting your industry
- Emerging trends that could impact your business
- Risk assessment to inform long-term security planning
- Business impact analysis of potential threats
Strategic intelligence helps shape your overall security strategy, resource allocation, and security policies. For SMB leadership, this intelligence translates complex security concepts into business risk terms that inform strategic decisions.
2. Tactical Intelligence
Tactical intelligence delivers detailed information about threat actor methodologies, tools, and techniques. Security professionals use tactical intelligence to:
- Understand specific attack methodologies
- Implement appropriate security controls
- Update detection and prevention technologies
- Develop effective defense strategies
This level of intelligence helps your IT and security teams stay ahead of evolving threats by understanding the specifics of how attackers operate.
3. Operational Intelligence
Operational intelligence provides actionable information about specific, immediate threats to your organization. This includes:
- Indicators of compromise (IoCs)
- Attack campaign details
- Imminent threat warnings
- Real-time attack patterns
For SMBs, operational intelligence enables rapid response to emerging threats before they cause significant damage.
4. Technical Intelligence
Technical intelligence focuses on the technical details of threats, including:
- Malware samples and analysis
- Vulnerability details
- Attack infrastructure
- Raw indicators like IP addresses and file hashes
Technical Data Insights helps technical teams implement specific defenses against known threat vectors.
For SMBs with limited resources, focusing initially on strategic and operational intelligence often provides the best return on investment, while gradually building capabilities in the other areas as resources permit.
Learn more about key concepts.
Understanding Cyber Risk Intelligence
A critical subset of CTI is cyber risk intelligence—information that helps you understand not just threats, but your specific vulnerabilities and the potential business impact of various attack scenarios.
Cyber risk intelligence helps SMBs:
- Identify and catalog critical business assets
- Understand the vulnerabilities affecting those assets
- Assess the likelihood of different attack scenarios
- Quantify the potential impact of successful attacks
- Prioritize remediation efforts based on business risk
For small businesses with limited resources, risk-based intelligence allows for smart allocation of security investments toward the threats that truly matter to your specific business.
Practical CTI Implementation for SMBs
Implementing cyber threat intelligence doesn’t have to be overwhelming. Here’s a practical, step-by-step approach tailored for SMBs:
1. Define Clear Objectives
Begin by establishing what you want to achieve with your CTI program:
- Are you primarily concerned with protecting customer data?
- Do you need to secure intellectual property?
- Are you focused on preventing business disruption?
- Do you need to meet specific compliance requirements?
Clear objectives keep your CTI program focused and prevent resource waste on threats that don’t meaningfully affect your business.
2. Identify Critical Assets and Threat Vectors
Next, catalog what matters most to your business:
- Customer information databases
- Financial systems
- Proprietary business processes
- Critical infrastructure
- Key personnel accounts
Identify and Protect For each asset, identify how attackers might target it and what impact a successful attack would have. This creates a practical framework for prioritizing intelligence.
3. Choose Appropriate CTI Tools and Services
SMBs have several cost-effective options for implementing CTI:
- Open-source intelligence feeds: Free resources that provide basic threat data
- Managed security service providers (MSSPs): Outsourced security that includes threat intelligence
- Industry-specific sharing groups: Collaborative intelligence specific to your sector
- Commercial CTI platforms: Scaled solutions with pricing tiers for smaller businesses
- Government resources: Many countries offer free CTI resources for small businesses
Start small with free or low-cost options, then expand as you demonstrate value and build capabilities.
4. Integrate CTI with Existing Security Infrastructure
Make CTI actionable by connecting it to your current security tools:
- Configure firewalls and intrusion detection systems to use threat indicators
- Update endpoint protection with the latest threat signatures
- Enhance email security with intelligence about phishing campaigns
- Strengthen access controls based on known attack patterns
Even basic security tools can become significantly more effective when informed by current threat intelligence.
5. Train Staff on CTI Processes
Your team needs to understand how to use threat intelligence effectively:
- Train IT staff to interpret and act on intelligence reports
- Educate non-technical staff about recognizing and reporting suspicious activity
- Develop basic response playbooks for common threat scenarios
- Conduct regular tabletop exercises to practice using intelligence in incident response
Remember that even the best intelligence is useless if your team doesn’t know how to apply it.
6. Continuously Monitor and Improve
Cyber threat intelligence is not a one-time implementation but an ongoing process:
- Regularly review the effectiveness of your CTI program
- Adjust intelligence sources based on their relevance to your business
- Update response procedures as new threats emerge
- Expand your program as resources allow
Start with the basics and gradually build more sophisticated capabilities as your program matures.
Leveraging Automation in Your CTI Program
Automation is a game-changer for SMBs implementing threat intelligence. With limited staff, automated tools can dramatically increase the effectiveness of your CTI program:
- Automated data collection: Tools that gather threat data from multiple sources
- Intelligence correlation: Systems that connect related threat indicators
- Automated alerts: Immediate notification of high-priority threats
