The Evolution of SocGholish and Its Growing Impact on Cybersecurity
SocGholish, operated by the notorious threat group TA569, has been a persistent force in the cybercrime landscape since its emergence in 2017. Known for its sophisticated JavaScript-based framework, SocGholish exploits legitimate websites to deploy malware disguised as critical system updates. Its adaptability and stealth have made it a preferred tool for financially motivated cybercriminals, posing a severe risk to organizations worldwide.
This blog delves into SocGholish’s latest tactics, recent developments, and its role as a gateway to more severe cyber threats—including ransomware and remote access trojans (RATs). As its infrastructure continues to expand and evolve, understanding its mechanisms and mitigation strategies is crucial for cybersecurity professionals, enterprises, and security researchers alike.
Understanding SocGholish
SocGholish, also known as FakeUpdates, is a sophisticated JavaScript-based framework utilized by financially motivated actors. Its primary method of operation involves social engineering tactics to compromise systems, often masquerading its payloads as critical system updates to deceive users into execution.
Key Characteristics of SocGholish
- Utilizes compromised legitimate websites to deliver malicious JavaScript
- Employs phishing emails to direct victims to these compromised sites
- Initiates a multi-stage infection process upon execution of fake updates
- Gathers detailed system information through Windows Management Instrumentation (WMI) calls
- Assesses the value of compromised systems to determine further actions
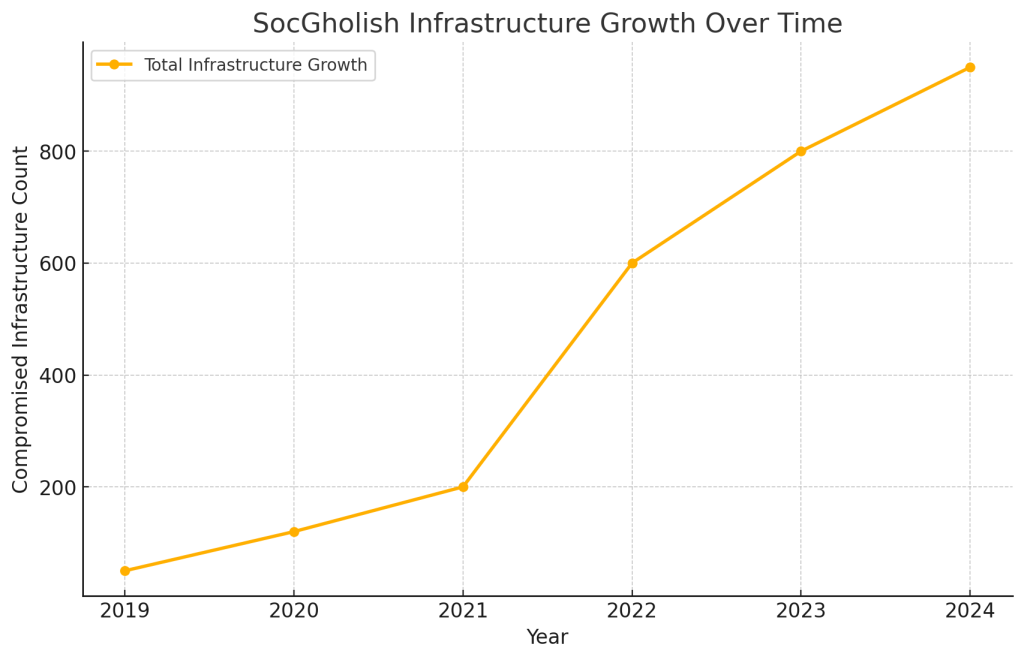
Recent Developments and Expansion
The threat landscape surrounding SocGholish has seen significant evolution in recent years:
- In 2022, there was a striking 334% increase in the infrastructure used by SocGholish operators
- The group began introducing an average of 18 new malware-staging servers per month
- A substantial number of these new servers were based in Europe, indicating a geographical expansion of operations
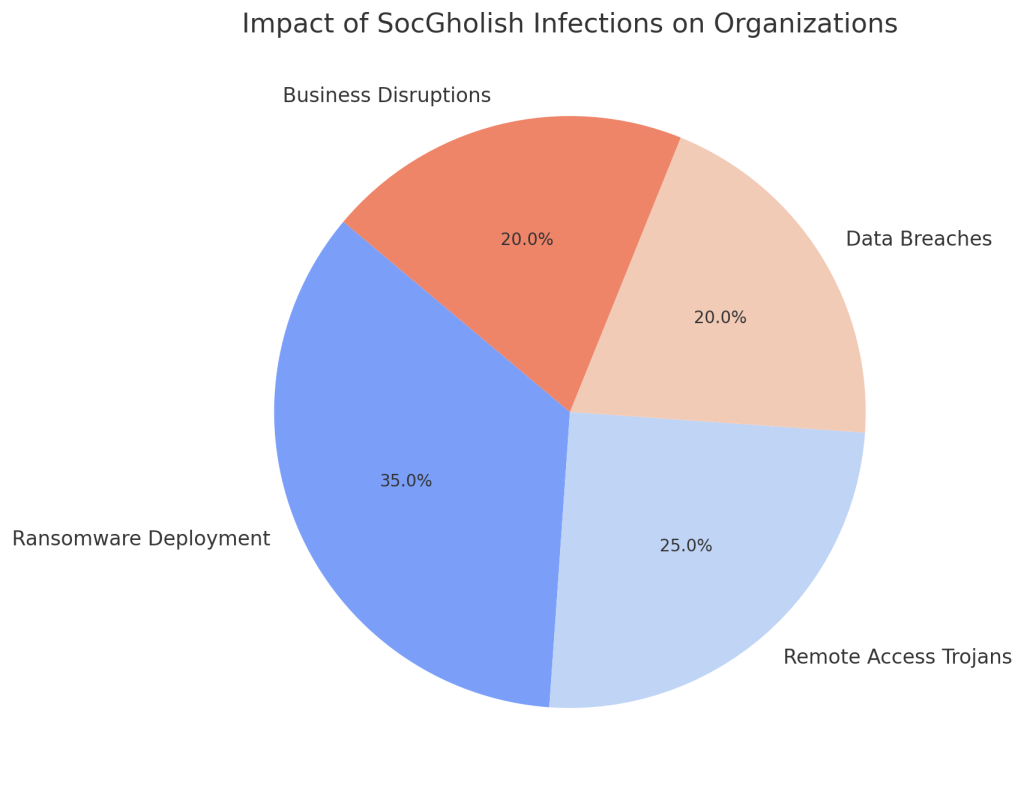
SocGholish as a Gateway Threat
One of the most concerning aspects of SocGholish is its role as a precursor to more severe cyber threats. Infections by SocGholish can lead to:
- Deployment of Remote Access Trojans (RATs)
- Ransomware infections
- Significant business disruptions
- Data breaches
- Reputational damage to affected organizations
Latest Cybersecurity Implications
While SocGholish remains a significant threat, recent developments in the cybersecurity landscape highlight the evolving nature of cyber threats:
An Iranian threat actor, identified as UNK_CraftyCamel, has been observed targeting organizations in the United Arab Emirates (UAE) using a sophisticated technique involving polyglot files to deliver a new backdoor called Sosano. This method, which is relatively uncommon in espionage attacks, demonstrates the increasing complexity of cyber threats facing organizations globally (SecurityWeek).
In a separate but equally concerning development, a cross-site scripting (XSS) vulnerability in Krpano software, widely used for creating virtual tours and VR environments, has been exploited to redirect users from compromised sites to arbitrary domains. This campaign has affected over 350 websites, including those of government organizations, universities, and Fortune 500 companies (SecurityWeek).
Mitigation Strategies
To protect against SocGholish and similar threats, organizations should implement robust cybersecurity measures, including:
- Comprehensive monitoring of network activities
- Regular employee training on identifying social engineering tactics
- Implementation of strong, layered security measures to prevent initial access by malicious JavaScript
- Regular audits of web server securities to detect and prevent vulnerabilities
- Keeping all software and systems up-to-date with the latest security patches
- Implementing strict access controls and the principle of least privilege
Conclusion
The persistence and evolution of threats like SocGholish, alongside the emergence of new sophisticated attack vectors, underscore the critical need for ongoing vigilance in cybersecurity. Organizations must remain proactive in their approach to security, continuously updating their defenses and educating their workforce to stay ahead of these ever-evolving threats.
As the digital landscape continues to expand and new vulnerabilities emerge, the importance of a comprehensive, adaptive cybersecurity strategy cannot be overstated. By staying informed about the latest threats and implementing robust security measures, organizations can better protect themselves against the complex and dynamic world of cyber threats.
